



Stop using a different policy language, policy model, and policy API for every product and service you use. Use OPA for a unified toolset and framework for policy across the cloud native stack.
Whether for one service or for all your services, use OPA to decouple policy from the service's code so you can release, analyze, and review policies (which security and compliance teams love) without sacrificing availability or performance.

Kubernetes
Envoy
Application
package application.authz
import future.keywords
# Everyone can see pets up for adoption
allowed_pets contains pet if {
some pet in input.pet_list
pet.up_for_adoption
}
# Employees can see all pets.
allowed_pets contains pet if {
[_, payload, _] := io.jwt.decode(input.token)
payload.employee
some pet in input.pet_list
}
Declarative. Express policy in a high-level, declarative language that promotes safe, performant, fine-grained controls. Use a language purpose-built for policy in a world where JSON is pervasive. Iterate, traverse hierarchies, and apply 150+ built-ins like string manipulation and JWT decoding to declare the policies you want enforced.
Context-aware. Leverage external information to write the policies you really care about. Stop inventing roles that represent complex relationships that years down the road no one will understand. Instead, write logic that adapts to the world around it and attach that logic to the systems that need it.

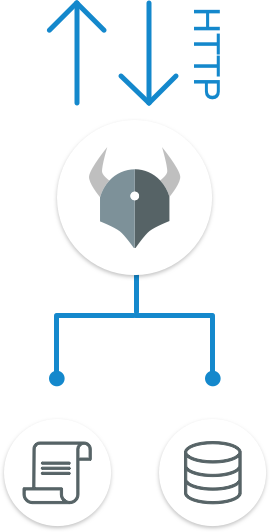
Deploy OPA as a separate process on the same host as your service. Integrate OPA by changing your service’s code, importing an OPA-enabled library, or using a network proxy integrated with OPA.

Embed OPA policies into your service. Integrate OPA as a Go library that evaluates policy, or integrate a WebAssembly runtime and use OPA to compile policy to WebAssembly instructions.
